Bad Rabbit Ransomware Attack

On October 14th, the Ukrainian Security Service warned that a new large scale cyber-attack, similar to notPetya, might take place sometime between October 13 and 17.
The attack arrived a few days later than expected; today (October 24th, 2017) the anticipated ransomware attack broke in Europe.
Ukraine was the main target for this malware, with many of its critical infrastructure such as train stations, airports and media sites suffering downtime. Other affected countries include Turkey, Russia and Bulgaria.
Affected companies include the Kiev Metro (Ukrainian train services), Odessa Airport (Ukraine), the Ukrainian ministries of infrastructure and finance and Interfax (a large Russian media outlet). And industries include Finance, Healthcare, Distribution and Software vendors.
Dubbed ‘BadRabbit’, the ransomware asks for a ransom payment of 0.05 BTC (~$280) in the first 40 hours of infection, after which the price will probably rise to a yet unknown amount.
The ransomware is being spread via a fake Flash software installer, which allegedly arrives as a pop-up from a legitimate Russian news site. Once run, the pop-up leads to a compromised site, which in turn downloads an executable dropper.
The ransomware uses a piece of known open source software called DiskCryptor in order to encrypt the victim’s drives.
The lock screen presented to the user is almost identical to the infamous Petya and NotPetya lock screens. However, this is the only similarity we have so far observed between the two malwares, in all other aspects BadRabbit is a completely new and unique ransomware.
After successful infection, the ransomware creates a unique key for each victim which is presented on a created ‘READ ME.txt’ file together with the payment site which is hosted on Tor. The payment site is very graphically appealing, using colorful and changing letters.
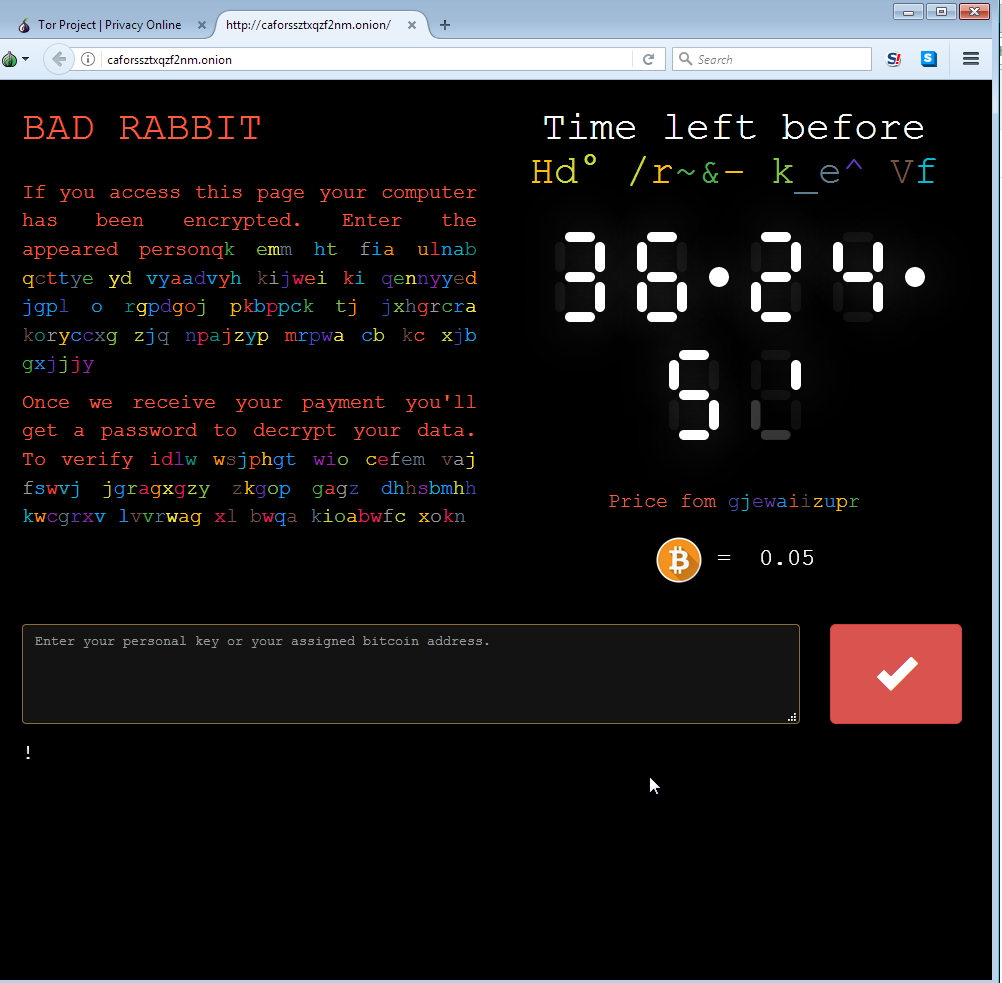
When entering the user key in the Tor payment site, each user receives a unique bitcoin wallet to which it is asked to transfer the payment of 0.05 BTC to.
Like WannaCry and Petya, the Bad Rabbit ransomware attack could have been prevented. Ransomware and other malwares are not the new normal. Watch this video to understand what ransomware is, and why being a target of cyber attacks is an unnecessary emergency. Then, read the whitepaper, “The Next Cyber Attack Can Be Prevented,” to learn five actionable strategies to avoid being tomorrow’s ransomware headline.
Check Point customers using the following products are protected against this threat:
- SandBlast Threat Emulation
- SandBlast Anti-Ransomware (this video shows how SandBlast blocks Bad Rabbit)
- Check Point Antivirus
Check Point IPS blade prevents this malware infection with these protections:
- Suspicious Executable Containing Ransomware
- Suspected Ransomware Dropzone
For the full research investigation into how Bad Rabbit operates, please see our research blog.
Posted in: Cyber Security
Leave a Comment (0) ↓
